Callback Encryption
Callback Encryption
Encryption is a security measure taken to protect sensitive data or private information. Callback encryption
ensures that the information being passed is protected by encryption, thus enhancing the security of communication between client and server.
Each parameter value can be encrypted in the callback configuration using supported algorithms and keys. Thus achieving security requirements over callback with reference to OpenSSL standards. This encryption can be achieved while triggering callback from IVR flow, Click to Call, or OBD API.
While creating Callback Profiles, clicking the Enable Encryption toggle button displays the fields related to encryption as shown in the following image. This is an optional field.
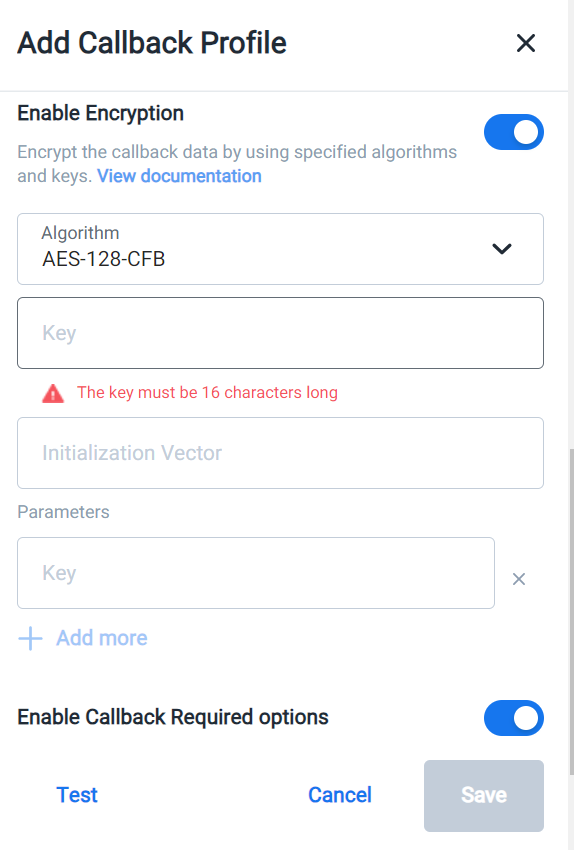
Prerequisites
To encrypt the parameter values, you need to send the required standard algorithms and keys to the Callback level along with the endpoint.
Algorithm
- AES (Advanced Encryption Standard) is an open-source symmetric encryption algorithm and it allows 128-bit, 192-bit, and 256-bit encryption. The format could be AES-128, AES-192, or AES-256.
- The mode of operation is encrypting the plain text into ciphertext using different modes. Kaleyra offers the following modes:
- GCM (Galois counter mode)—GCM encryption algorithm combines two modes; the counter mode and the new Galois mode of authentication. The parallel computation enabled in the latest mode ensures higher-speed encryption with higher throughput than other encryption algorithms like CFB.
- CFB (Ciphertext feedback)—CFB algorithms can only be parallelized in the decryption process and not in the encryption process, therefore they run with a slower performance than other algorithms such as those in mode GCM.
Descriptions of the algorithms available are as follows:
| Algorithm | Description |
|---|---|
| AES-128-CFB | With this algorithm, only the decryption process can be parallelized and not the encryption process. The key length is 128 bits. |
| AES-128-GCM | With this algorithm, both decryption and encryption processes can be parallelized, allowing higher throughput. The key length is 128 bits. |
| AES-192-CFB | With this algorithm, only the decryption process can be parallelized and not the encryption process. The key length is 192 bits. |
| AES-192-GCM | With this algorithm, both decryption and encryption processes can be parallelized, allowing higher throughput. The key length is 192 bits. |
| AES-256-CFB | With this algorithm, only the decryption process can be parallelized and not the encryption process. The key length is 256 bits. |
| AES-256-GCM | With this algorithm, both decryption and encryption processes can be parallelized, allowing higher throughput. The key length is 256 bits. |
Key
- A unique secret key needs to be passed along with the algorithm for encryption in the callback configuration.
- The length of this key will depend on the algorithm selected, the options are:
- AES-128 (Length will be 16)
- AES-192 (Length will be 24)
- AES-256 (length will be 32)
Initialization Vector
- This is used to prevent a sequence of text that are identical from generating the same ciphertext when encrypted.
- The length of the Initialization vector should be 16.
- This is a mandatory factor.
Updated 8 months ago
